Video•Mar 2, 2026
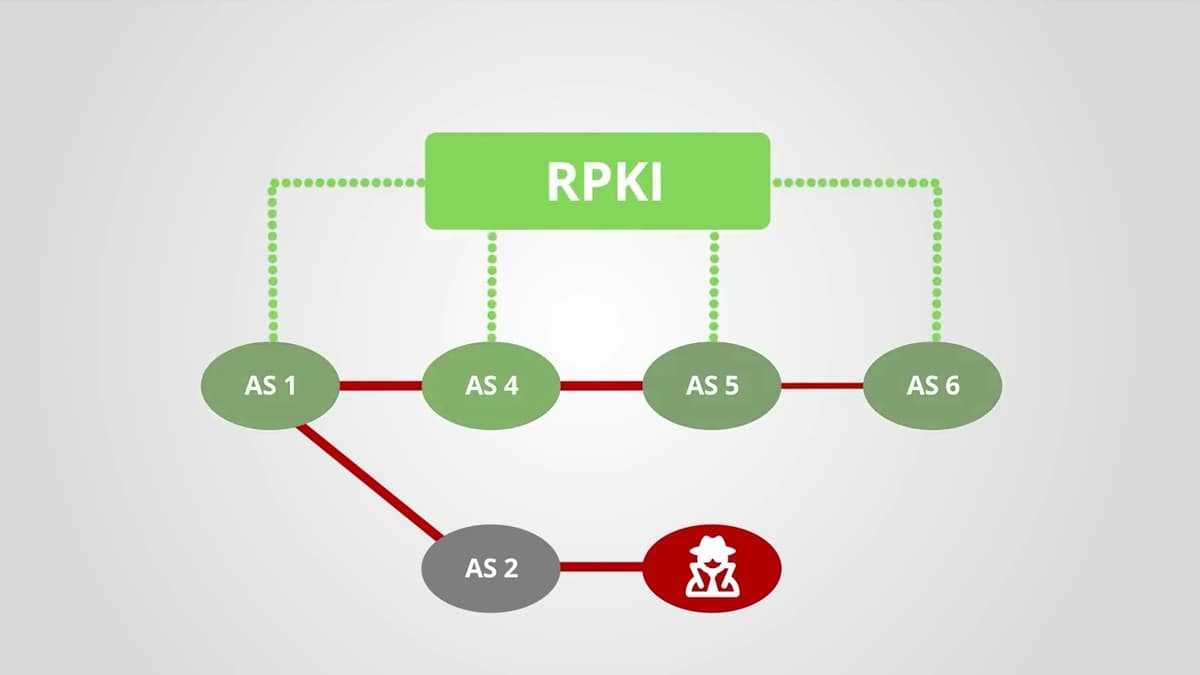
How Does RPKI Help with Routing Security?
The video explains that the Border Gateway Protocol (BGP), the Internet’s routing backbone, was designed without security features, allowing any autonomous system to announce any IP prefix and creating a systemic vulnerability. It introduces the Resource Public Key Infrastructure (RPKI) as a cryptographic framework that issues digital certificates for IP address blocks and AS numbers. These certificates enable Local Internet Registries (LIRs) to create signed route origin authorizations, which are published in publicly accessible repositories. The presenter highlights that network operators download and validate these authorizations, performing BGP origin validation to discard illegitimate announcements. Real‑world hijack incidents are cited as examples of attacks that RPKI can prevent. By filtering bogus routes, RPKI restores inter‑provider trust, reduces the risk of large‑scale hijacks, and is becoming essential for a resilient Internet, prompting carriers to adopt validation policies.
By RIPE NCC
Video•Mar 1, 2026
Why Is a WAF No Longer Enough?
Enterprises are discovering that traditional Web Application Firewalls (WAFs) no longer provide sufficient protection against today’s complex threat landscape. The video explains that a WAF, originally designed to filter malicious HTTP traffic, is an outdated term as application security now...
By David Bombal
Video•Feb 28, 2026
Physical Partitioning Is a Real Security Strategy for OpenClaw Agents
The video explains a security‑first approach to managing OpenClaw agents by physically partitioning their access and responsibilities. The creator has instantiated multiple agents—Sylvie for homeschooling content and Finn for accounting—each confined to its own “family vault,” ensuring that data never...
By How I AI

Video•Feb 28, 2026
Black Hat USA 2025 | If Google Uses It to Find Webpages, We Can Use It to Find Fraudsters
The session at Black Hat USA 2025 introduced a surprisingly simple technique—term‑frequency inverse‑document‑frequency (TF‑IDF)—as a powerful tool for spotting fraudsters, positioning it as an alternative to the sophisticated AI browsers and agents that dominate today’s web search. Speakers argued that generative...
By Black Hat
Video•Feb 28, 2026
Compliant or Facing Federal Fines
The video warns government contractors that false claims about cybersecurity compliance can trigger severe penalties under the False Claims Act, especially as the Department of Defense’s CMMC framework becomes contractually mandatory. In 2025, whistleblower‑driven actions resulted in $6.8 billion in fines across...
By Paul Asadoorian

Video•Feb 28, 2026
HackTheBox - Guardian
The HackTheBox "Guardian" walkthrough demonstrates a full‑stack penetration test, starting with network scanning and sub‑domain discovery that revealed a default credential (GU1234). Attackers leveraged FFUF to brute‑force accounts, accessed a chat feature, and uncovered a Gitea instance where the public...
By IppSec
Video•Feb 28, 2026
Techstrong TV - February 27, 2026
Techstrong TV featured Nikquille Hondigal, co‑founder and Chief AI Officer of Forward Networks, to discuss the company’s evolution from a software‑defined networking (SDN) startup to an AI‑enabled network operations provider. Founded twelve years ago by Stanford PhDs, Forward Networks has...
By Techstrong TV (DevOps.com)
Video•Feb 27, 2026
Phone Travel Safety
The video addresses a common concern for travelers: keeping a smartphone secure while on the road. It emphasizes that the simplest line of defense is to rely on the carrier’s 4G/5G network rather than public Wi‑Fi, and to employ a...
By PCWorld
Video•Feb 27, 2026
Patch and Threat Hunt Immediately
The video warns of a newly disclosed vulnerability in Cisco’s Catalyst SD‑WAN controller and manager that grants unauthenticated attackers full administrative rights. Rated a perfect 10 on severity, the flaw has been weaponized for three years and may already reside...
By Simply Cyber
Video•Feb 27, 2026
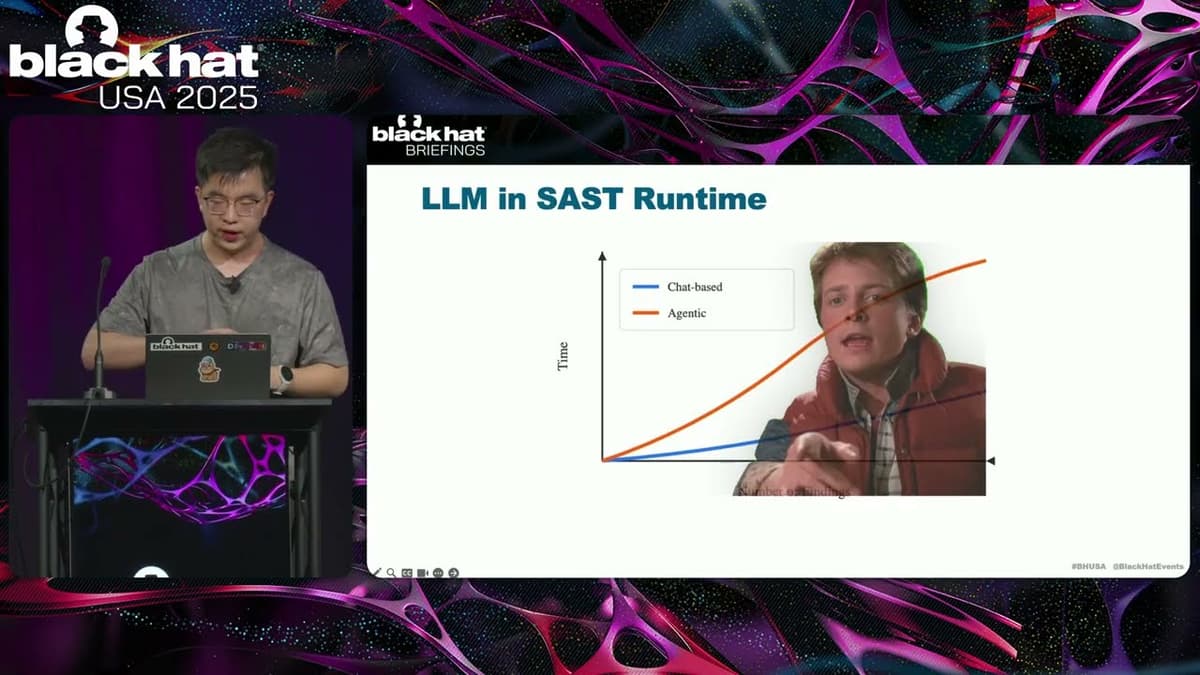
Black Hat USA 2025 | Let LLM Learn: When Your Static Analyzer Actually 'Gets It'
The Black Hat presentation explored how large language models (LLMs) can be fused with traditional static analysis tools to create a new generation of vulnerability scanners. The speaker outlined three integration patterns—AI‑enhanced, where a static scanner filters LLM output; AI‑explorer,...
By Black Hat
Video•Feb 27, 2026
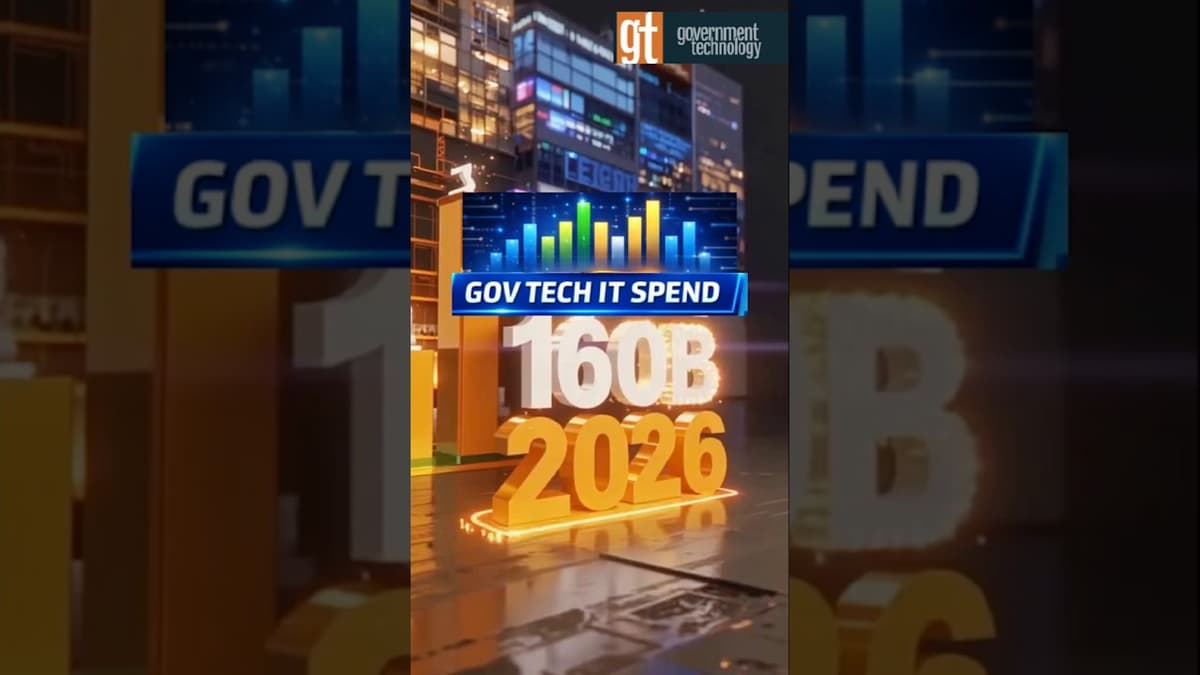
GT Fast5: $160B in Government Tech Spending Ahead — Are States Ready? #Accessibility #AI #Shorts
The video outlines a looming $160.2 billion federal IT spend in 2026, highlighting an April deadline for states to make all websites and apps accessible to people with disabilities. It frames the spending surge as part of a broader push to...
By Government Technology (GovTech Magazine)

Video•Feb 27, 2026
ContinuumCon Prep (with Greg Ake!)
ContinuumCon is a newly‑minted virtual cybersecurity conference that flips the traditional lecture‑heavy format on its head, delivering fully hands‑on workshops where attendees work directly with presenters in real time. The event is organized by Greg Ake of Level Effect...
By John Hammond
![H?ckers A[r]e Gl*bbing](/cdn-cgi/image/width=1200,quality=75,format=auto,fit=cover/https://i.ytimg.com/vi/IImLVU39V_Q/maxresdefault.jpg)
Video•Feb 27, 2026
H?ckers A[r]e Gl*bbing
The video introduces LOLGlobs, a community‑driven repository that catalogs wildcard‑based command‑line obfuscation techniques for Linux, macOS, Windows CMD, and PowerShell. Originating from a security‑operations Slack channel and authored by HexV1N at ReliaQuest, the project builds on earlier efforts like Argfuscator...
By John Hammond
Video•Feb 26, 2026
Thousands of Google API Keys Exposed
A recent investigation uncovered thousands of Google API keys publicly exposed in code repositories and configuration files. While Google historically treated API keys as non‑secret identifiers, the launch of Gemini’s AI services now allows those keys to access billable resources,...
By John Hammond
Video•Feb 26, 2026
Techstrong TV - February 25, 2026
Techstrong TV hosted Darren Williams, founder and CEO of Blackfog, to discuss the company’s origin, its endpoint‑focused anti‑exfiltration technology, and the firm’s annual State of Ransomware 2025 report ahead of RSA. Williams explained that traditional data‑loss‑prevention tools falter because they sit...
By Techstrong TV (DevOps.com)