
Blog•Mar 2, 2026
Quantum-Secure Cloud Computing: The Next Frontier in Enterprise Data Protection
A consortium of leading tech firms and universities launched a quantum‑secure cloud computing framework that embeds post‑quantum cryptography into existing cloud stacks. The hybrid model delivers lattice‑based encryption and dynamic key management while adding less than 5% latency. Early pilots are underway with AWS, Google Cloud, and Microsoft Azure, and financial and healthcare firms are among the first adopters. Analysts project a market exceeding $15 billion for quantum‑resistant cloud solutions by 2028.
By Ian Khan’s Technology Blog
Blog•Mar 1, 2026
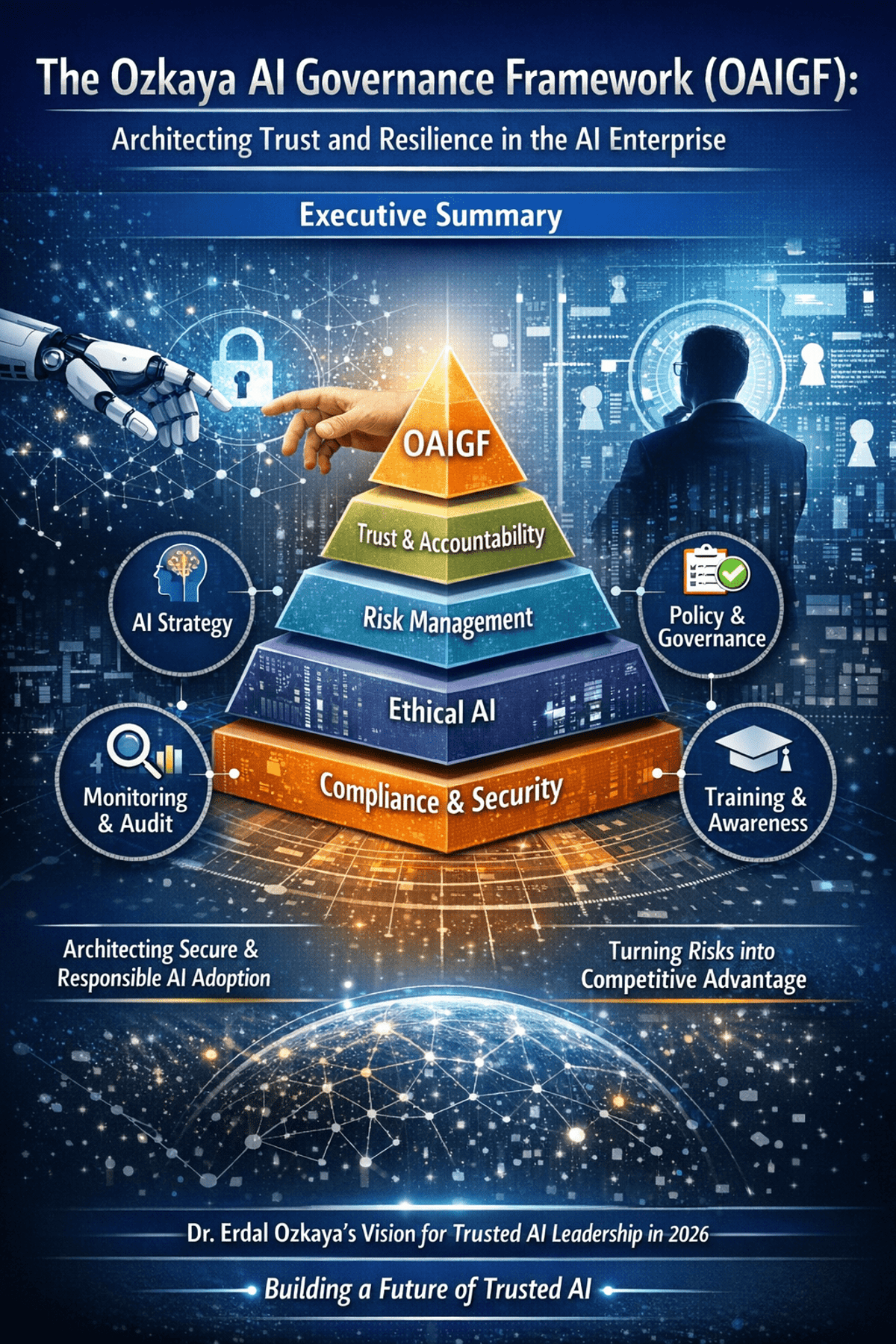
The Ozkaya AI Governance Framework (OAIGF): Architecting Trust and Resilience in the AI Enterprise
The Ozkaya AI Governance Framework (OAIGF) is a practitioner‑driven methodology that equips CISOs with a comprehensive blueprint for secure, ethical, and compliant AI deployment at enterprise scale. Building on standards such as NIST AI RMF and ISO/IEC 42001, the framework defines...
By Erdal Ozkaya’s Cybersecurity Blog
Blog•Mar 1, 2026
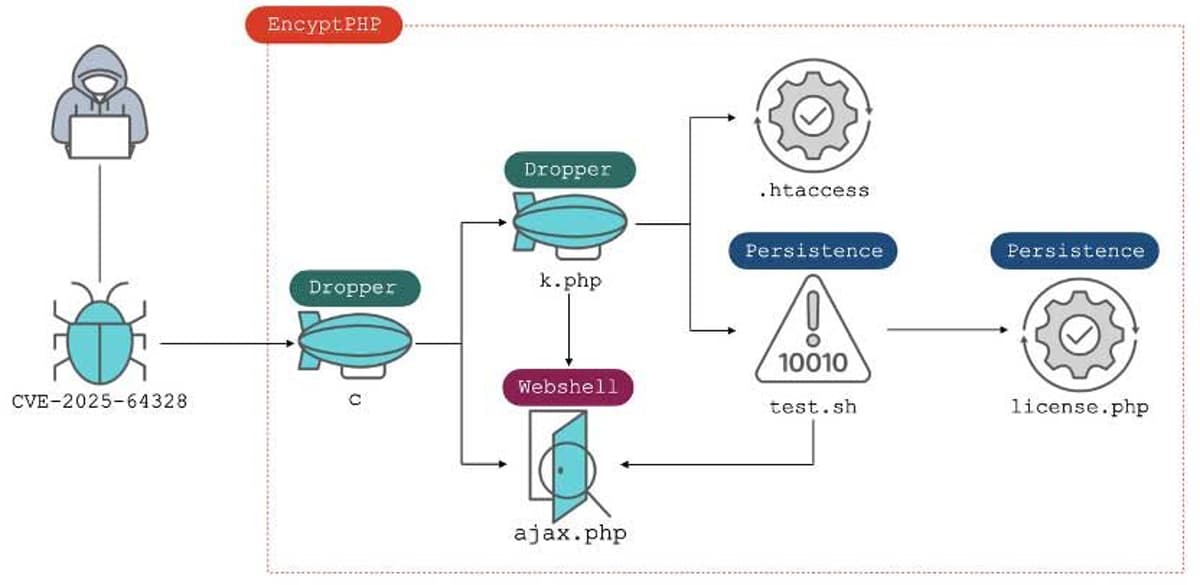
CVE-2025-64328 Exploitation Impacts 900 Sangoma FreePBX Instances
Around 900 Sangoma FreePBX installations were compromised after attackers leveraged CVE-2025-64328, a post‑authentication command‑injection flaw in the Endpoint Manager module. The vulnerability, rated 8.6 on the CVSS scale, allowed malicious code execution and led to the deployment of the EncystPHP...
By Security Affairs

Blog•Feb 28, 2026
RaspyJack : Tiny Raspberry Pi Zero 2W Network Toolkit for Security Testing & More
The RaspyJack is an open‑source, handheld network toolkit built around the Raspberry Pi Zero 2W. It combines a Waveshare 1.44‑inch LCD, a TP‑Link AC1300 dual‑band USB adapter, and a Pi Sugar power module for portable, field‑ready security testing. The device runs Linux utilities for...
By Geeky Gadgets

Blog•Feb 28, 2026
Who Is the Kimwolf Botmaster “Dort”?
KrebsOnSecurity identified the individual behind the Kimwolf botnet as a teenager from Canada using the handle "Dort" and aliases like CPacket and M1CE. Public OSINT links the persona to a GitHub account, multiple cyber‑crime forum registrations, and a history of...
By Krebs on Security

Blog•Feb 28, 2026
Iran ’S Internet Near-Totally Blacked Out Amid US, Israeli Strikes
Iran experienced a near‑total internet blackout on Feb. 28, 2026, as U.S. and Israeli strikes hit the country. Network monitoring by NetBlocks showed national connectivity dropping to roughly 4% of normal levels, while Cloudflare reported traffic falling to effectively zero...
By Security Affairs

Blog•Feb 27, 2026
Cybersecurity and AI in the Era of Home-Based Care Logistics
Kenco’s vice‑president of life sciences, Tim McClatchy, detailed how the firm is hardening cybersecurity across its manufacturer‑to‑home delivery network while deploying AI to streamline labor planning and route optimization. He explained the specific encryption and verification steps used at each...
By Pharmaceutical Commerce (independent trade)

Blog•Feb 27, 2026
SEALSQ Expands Japan Presence to Support 2035 Quantum Security Mandate
SEALSQ Corp is expanding its footprint in Japan by showcasing its production‑ready QS7001 secure System‑on‑Chip and QVault Trusted Platform Module at two March 2026 industry events. The move backs Japan’s National Cyber Command Office mandate to transition all government and critical‑infrastructure...
By Quantum Zeitgeist
Blog•Feb 27, 2026
Quantum eMotion Strengthens Cybersecurity Strategy with SecureKey Platform Acquisition
Quantum eMotion Corp. announced the acquisition of SKV Technology Inc., securing the SecureKey platform and its memory‑less cryptographic suite. The deal merges QeM’s Sentry‑Q quantum‑grade entropy layer with SecureKey’s hardware‑integrated enforcement, delivering a full‑stack, quantum‑resilient security architecture from cloud to...
By Quantum Zeitgeist
Blog•Feb 27, 2026
Weekly Wrap: Resilience Is the New Spectrum Policy Buzzword
The EU’s Digital Networks Act (DNA) is being positioned as a cornerstone for simplifying telecom regulations and reducing market fragmentation across member states. At the Future Connectivity Summit, regulators emphasized the Act’s role in fostering spectrum coherence while also highlighting...
By PolicyTracker blog

Blog•Feb 27, 2026
Phishing Attacks Against People Seeking Programming Jobs
A wave of phishing campaigns is targeting individuals searching for programming jobs, using fabricated job listings to harvest credentials. At the same time, North Korean APT37 has released new tools that weaponize removable media, raising concerns about air‑gap breaches. The...
By Schneier on Security
Blog•Feb 27, 2026
How AI Aids Incident Response: Why Humans Alone Cannot Do IR Efficiently
Incident response traditionally relies on manual log correlation, alert validation, and report drafting, consuming 10‑20 minutes per case and often days for complex attacks. AI‑enabled platforms now ingest telemetry from SIEM, EDR, identity, and cloud sources the moment an alert...
By Security Affairs
Blog•Feb 27, 2026
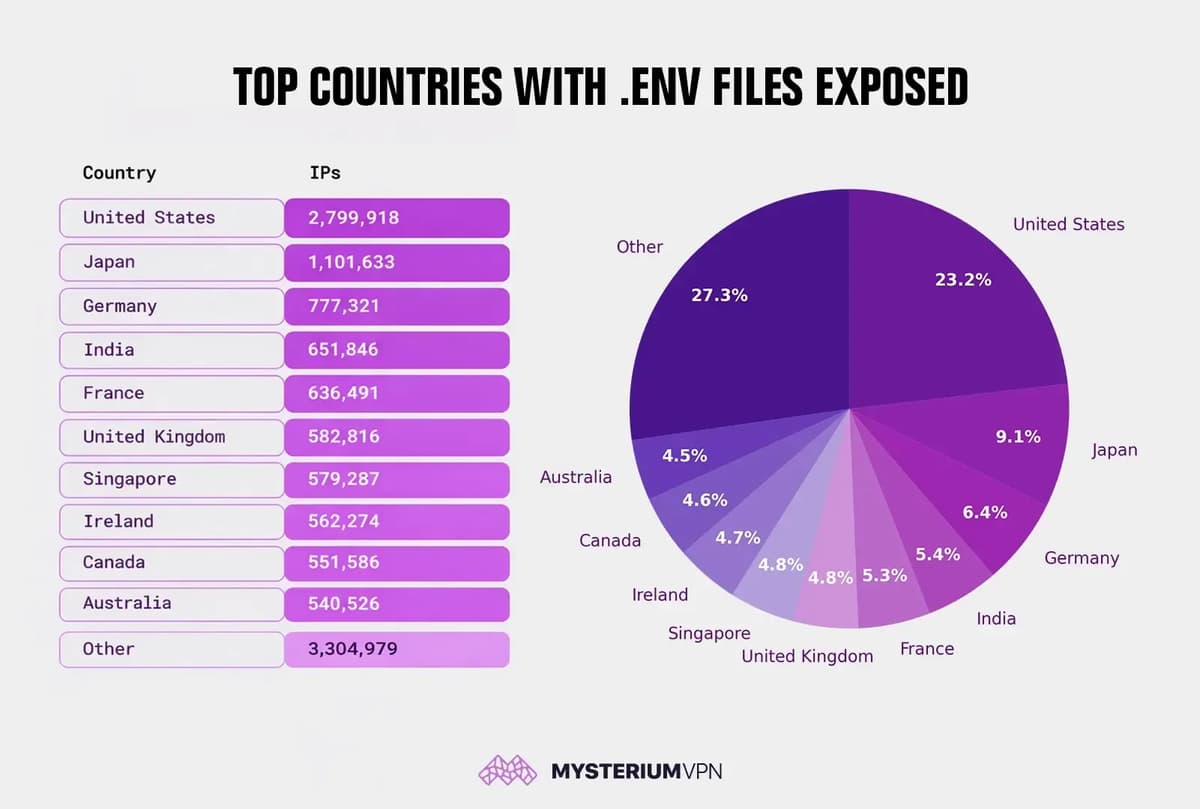
12 Million Exposed .env Files Reveal Widespread Security Failures
Mysterium VPN’s research uncovered more than 12 million IP addresses serving publicly accessible .env‑style files, leaking credentials such as database passwords, API keys, and JWT signing secrets. The United States leads the exposure count with roughly 2.8 million IPs, while Japan, Germany,...
By Security Affairs

Blog•Feb 27, 2026
RefAssured, ID.me Partner to Fight Candidate Fraud
RefAssured and ID.me have launched an advanced fraud‑prevention solution that embeds identity verification into staffing agencies' existing applicant tracking systems. The joint offering combines RefAssured’s 1.5 million reference reports with ID.me’s digital identity wallet, which serves over 160 million users, to authenticate...
By HRTech Cube

Blog•Feb 27, 2026
Beyond the CLI: 5 Governance Questions Every CISO Must Ask Before Deploying Claude Code
Anthropic’s Claude Code introduces a CLI‑based AI agent that can navigate repositories, draft patches, and run tests, turning code remediation into a near‑instant process. While the speed gains are compelling, the tool also grants autonomous execution rights that blur traditional...
By Erdal Ozkaya’s Cybersecurity Blog